misc formatting |
Add router configurations for pfSense and OPNsense |
||
| (33 intermediate revisions by 8 users not shown) | |||
| Line 1: | Line 1: | ||
< | <languages/> | ||
== HTTP & WebSocket Traffic == <!--T:2--> | <translate><!--T:1--> Resonite is a feature rich engine that is connected both to other users and the Resonite cloud services. If you're concerned or have a firewall you'd like to configure then read on to find out more.</translate> | ||
== <translate><!--T:58--> HTTP & WebSocket Traffic</translate> == <!--T:2--> | |||
<!--T:3--> | <!--T:3--> | ||
Things like | <translate><!--T:59--> Things like messages, profile information and items in your inventory are all stored within the Resonite cloud. Your copy of Resonite will use HTTP(S) or WebSockets to retrieve this information.</translate> | ||
<!--T: | <translate><!--T:60--> Here is a list of places you might see connections to:</translate> | ||
== Session Traffic == <!--T:5--> | * <translate><!--T:61--> Most HTTPS Traffic is from <code>api.resonite.com</code></translate> | ||
* <translate><!--T:62--> SignalR (real time updates) makes a WebSocket connection to the Microsoft managed service also at <code>api.resonite.com</code></translate> | |||
* <translate><!--T:63--> Assets (avatars, meshes, textures etc.) and other blobs (large files) come from a variety of hosts:</translate> | |||
** <translate><!--T:64--> Asset variants are stored at <code>variants.resonite.com</code> and <code>skyfrost-archive.resonite.com/variants</code></translate> | |||
** <translate><!--T:65--> Assets are stored at <code>assets.resonite.com</code> and <code>skyfrost-archive.resonite.com/assets</code></translate> | |||
** <translate><!--T:66--> Thumbnails are stored at <code>thumbnails.resonite.com</code> and <code>skyfrost-archive.resonite.com/thumbnails</code></translate> | |||
== <translate><!--T:67--> Session Traffic</translate> == <!--T:5--> | |||
<!--T:6--> | <!--T:6--> | ||
When you connect to a Resonite session, you're starting a connection to the | <translate><!--T:68--> When you connect to a Resonite session, you're starting a connection to the session's host. This is usually another user's computer but sometimes can be a headless session which could be hosted in a number of places - two of the most common ones being on someone's spare computer or on a computer rented in a data center.</translate> | ||
<translate><!--T:69--> Depending on your settings and the settings of the session host you'll connect with either one of the following protocols:</translate> | |||
* [https://github.com/RevenantX/LiteNetLib LNL (LiteNetLib)] | * [https://github.com/RevenantX/LiteNetLib LNL (LiteNetLib)] | ||
* [https://partner.steamgames.com/doc/features/multiplayer/networking Steam Sockets]. Sometimes called "Steam Networking Sockets", "Steam Network", "SNS" etc. | * [https://partner.steamgames.com/doc/features/multiplayer/networking Steam Sockets]. <translate><!--T:70--> Sometimes called "Steam Networking Sockets", "Steam Network", "SNS" etc.</translate> | ||
=== LNL === <!--T:7--> | === LNL === <!--T:7--> | ||
<!--T:8--> | <!--T:8--> | ||
* [https://github.com/RevenantX/LiteNetLib LNL] uses UDP to connect. | * <translate><!--T:71--> [https://github.com/RevenantX/LiteNetLib LNL] uses UDP to connect.</translate> | ||
* Ports will vary and can be any port depending on the host as it lets the host pick a free port | * <translate><!--T:72--> Ports will vary and can be any port depending on the host as it lets the host pick a free port</translate> | ||
* In other cases a relay will be used. | * <translate><!--T:73--> In other cases a relay will be used.</translate> | ||
* | * <translate><!--T:74--> After [https://en.wikipedia.org/wiki/Hole_punching_(networking) punch-through] or relay, the actual connection to the user can be any IP or port.</translate> | ||
=== <translate><!--T:75--> Steam Sockets</translate> === <!--T:9--> | |||
<translate><!--T:76--> Steam Sockets is a Valve created networking protocol. You can find information on it [https://github.com/ValveSoftware/GameNetworkingSockets here]</translate> | |||
== <translate><!--T:77--> Establishing Connections</translate> == | |||
<translate><!--T:78--> Resonite utilizes multiple methods to attempt to connect users to sessions on remote machines. This can be illustrated in the following flow chart.</translate> | |||
{{Diagram:LNLConnectionOptions{{UseLangLink}}}} | |||
<translate><!--T:31--> Resonite will attempt to directly connect users where it can, for example over a LAN. However, this is not always possible due to a variety of network security constraints.</translate> | |||
=== Direct IP === <!--T:30--> | |||
=== <translate><!--T:79--> Direct IP</translate> ===<!--T:30--> | |||
<!--T:51--> | <!--T:51--> | ||
In general, direct is best. You’re connecting directly with the remote server and are telling Resonite exactly where to go and how to get there (you are connecting with a direct IP address or domain name). | <translate><!--T:80--> In general, direct IP is best. You’re connecting directly with the remote server and are telling Resonite exactly where to go and how to get there (you are connecting with a direct IP address or domain name).</translate> | ||
<!--T:52--> | <!--T:52--> | ||
To use direct IP | <translate><!--T:81--> To use direct IP</translate> | ||
* Use an OpenWorld ProtoFlux node | * <translate><!--T:82--> Use an OpenWorld ProtoFlux node and add a Uri (purple input second from top) with the IP address and port like this: <code>lnl://<IPv4 address>:<Port>/</code></translate> | ||
** For IPv6, wrap the address in brackets | ** <translate><!--T:83--> For IPv6, wrap the address in brackets <code>lnl://[<IPv6 address>]:<port>/</code></translate> | ||
** | ** <translate><!--T:84--> You can also use a DNS record for this - <code>lnl://<domain>:<port>/</code></translate> | ||
* A port is currently required as part of the URL | * <translate><!--T:85--> A port is currently required as part of the URL</translate> | ||
* This is mostly applicable to headless sessions | * <translate><!--T:86--> This is mostly applicable to headless sessions where the session has a static IP address and port. Keep an eye out for session owners providing items that include direct links for their worlds as that will be the most reliable and expedient way to connect to said world.</translate> | ||
<translate><!--T:87--> As an example for a session hosted with the IPv4 address <code>203.0.113.7</code>, IPv6 address <code>2001:db8::7</code>, the DNS record <code>seven.example.com</code> on port <code>12100</code>:</translate> | |||
<code>lnl:///203.0.113.7:12100/</code>: <translate><!--T:88--> IPv4 direct connection</translate> | |||
<code>lnl://[2001:db8::7]:12100/</code>: <translate><!--T:89--> IPv6 direct connection</translate> | |||
<!--T: | <code>lnl://seven.example.com:12100/</code>: <translate><!--T:90--> DNS direct connection</translate> | ||
=== NAT Punchthrough === <!--T:40--> | === <translate><!--T:91--> UDP Hole Punching (LNL NAT Punchthrough)</translate> === <!--T:40--> | ||
<!--T:54--> | <!--T:54--> | ||
<translate><!--T:92--> UDP hole punching is used by LNL in Resonite in order to establish a bidirectional connection between you and a session host where Network Address Translation (NAT) is in play on one or both sides of a connection.</translate> | |||
<translate><!--T:93--> This is facilitated by one of Resonite's LNL punchthrough servers (the same hosts that can be seen in [[#LNL Relay]]), where both you and the host establish a connection in order to establish a peer to peer connection between you and the host that should be indistinguishable from directly connecting.</translate> | |||
<!--T:55--> | <!--T:55--> | ||
If you encounter NAT | <translate><!--T:94--> If you encounter issues with NAT punchthrough, you may be behind a Strict (also known as Type 3) NAT, where the conditions of the NAT make it so hole punching doesn't work.</translate> | ||
<translate><!--T:95--> You can check your NAT type by going to https://networktest.razortune.com/ in a web browser - this is a tool hosted by community member Rucio and is specific towards Resonite networking.</translate> | |||
<translate><!--T:96--> If your NAT type is Strict, there are two common causes for this:</translate> | |||
* <translate><!--T:97--> Your router could have settings in place for its NAT causing this to happen - what you want is a 1:1 NAT or a static NAT (terminology may differ depending on router)</translate> | |||
* <translate><!--T:98--> Your ISP could be doing CGNAT in a way that causes this - you can see if you're behind CGNAT by checking what your router reports your WAN address as being and what a site like https://ipinfo.io says; if these two addresses differ, you're likely behind CGNAT.</translate> | |||
If | <translate><!--T:99--> If it's your router:</translate> | ||
* Your router | |||
<translate><!--T:100--> Check your router settings - a good way to start is by searching "<router> Open NAT" and seeing what comes up setting wise.</translate> | |||
<translate><!--T:101--> If it's your ISP:</translate> | |||
<translate><!--T:102--> You may be able to contact your ISP to get them to either take you out from behind CGNAT or give you a static, public IPv4 address. This may come at a cost for something like a static IP.</translate> | |||
<translate><!--T:103--> If you're unable to resolve being in a strict NAT situation, it is recommended to use [[#Direct IP]] connections followed by using the [[#LNL Relay]] to connect to sessions.</translate> | |||
<!--T:56--> | <!--T:56-->=== <translate><!--T:104--> Possible Bugs</translate> === | ||
<!--T:57--> | * <translate><!--T:57--> One current issue seems to be that the NAT punchthrough server occasionally does not respond very quickly, and the client does not always wait for a response and tries the next protocol on it’s internal list to attempt.</translate> | ||
=== LNL Relay === <!--T:50--> | * <translate><!--T:105--> The punchthrough server does not support IPv6, instead only supporting IPv4. Some ISPs in some parts of the world, such as Japan, use exclusively IPv6. Users in these networks may not be able to use NAT punchthrough (this gets very complicated very quickly, results will vary). [https://github.com/Yellow-Dog-Man/Resonite-Issues/issues/143 (Github Issue #143)]</translate> | ||
=== <translate><!--T:106--> LNL Relay</translate> === <!--T:50--> | |||
<!--T:58--> | <!--T:58--> | ||
This | <translate><!--T:107--> This can come with performance implications. The relay acts as a third point between both clients, and all traffic is routed through it. Ping will likely be worse here (but not always). If the relay has issues or is overloaded, you may also get service issues.</translate> | ||
* <translate><!--T:108--> We have the following LNL Relays</translate> | |||
** uswest1.resonite.com - <translate><!--T:109--> US West (Hillsboro, OR)</translate> | |||
** au1.resonite.com - <translate><!--T:110--> Oceania (Sydney, Australia)</translate> | |||
** japan1.resonite.com - <translate><!--T:111--> Asia Pacific (Tokyo, Japan)</translate> | |||
** europe.resonite.com - <translate><!--T:112--> Europe (Helsinki, Finland)</translate> | |||
<translate><!--T:113--> You can see the status of these relays at https://status.yellowdogman.com or in a raw format at https://api.resonite.com/networknodes</translate> | |||
==== <translate><!--T:114--> How LNL Relays Work</translate> ==== | |||
<translate><!--T:115--> When a relay is required, the client sends a request to https://api.resonite.com/networknodes to retrieve the currently available relays. From there, the client makes a determination based upon multiple factors which relay is the best one for it to utilize. For example, the relay's currently available capacity, and its ping. The ports for the relay are determined by the relay server's operating system and port availability. Do not assume any consistency for the relays.</translate> | |||
<translate><!--T:116--> Here's a diagram illustrating the relay connection flow:</translate> | |||
== Recommendations for Headless Servers == <!--T:21--> | {{Diagram:LNLRelayConnection{{UseLangLink}}}} | ||
<translate><!--T:117--> At this time, we do not support the ability to pick a specific relay.</translate> | |||
== <translate><!--T:118--> Recommendations for Headless Servers</translate> == <!--T:21--> | |||
<!--T:59--> | <!--T:59--> | ||
To better support direct connection conditions it is suggested server hosts try to promote direct IP connections and IPv6 support. | <translate><!--T:119--> To better support direct connection conditions it is suggested server hosts try to promote direct IP connections and IPv6 support.</translate> | ||
<translate><!--T:120--> If you have a public IPv4 address that you can use, you can port forward the session's port. To do this, set the <code>forcePort</code> option for the world in your headless config file & forward the port through your router. You can find out how to do this by searching "<Router Model> port forward" - for most routers, you'll be able to find an example somewhere on the internet.</translate> | |||
<translate><!--T:121--> If you have IPv6 support, use it when possible by setting <code>forcePort</code> as in the IPv4 example, allowing the session's port through your firewall & direct connecting (See [[#Direct IP]] for how to directly connect to a session)</translate> | |||
<!--T: | <translate><!--T:122--> You may not be to port forward in all situations, such as if you're using a router that doesn't let you port forward or if you're behind CGNAT.</translate> | ||
<translate><!--T:123--> If you are behind CGNAT (Carrier Grade NAT), see if you can get off it - depending on your ISP and the type of your internet connection, you may get varying results. Some will take you off CGNAT if you ask, some will get you to pay for a static IP address and some may not allow you to get off CGNAT at all.</translate> | |||
== Recommended Router Configuration == <!--T:10--> | |||
<translate><!--T:124--> If you're having users with issues connecting via LNL punchthrough, direct them to directly connecting to your session. Making an object that connects them - such as a button that they can press and just connect makes doing this quite easy.</translate> | |||
== <translate><!--T:125--> Recommended Router Configuration</translate> == <!--T:10--> | |||
<!--T:11--> | <!--T:11--> | ||
Many consumer routers are configured by default to provide optimal connectivity for Resonite by routing traffic in such a way which permits the ability for users to directly establish a connection to other users on the Internet. However, some advanced routers employ a type of NAT (Network Address Translation) where port numbers are not preserved when communicating with other hosts on the | <translate><!--T:126--> Many consumer routers are configured by default to provide optimal connectivity for Resonite by routing traffic in such a way which permits the ability for users to directly establish a connection to other users on the Internet. However, some advanced routers employ a type of NAT (Network Address Translation) where port numbers are not preserved when communicating with other hosts on the internet. This type of NAT is often referred to as strict, or “Type-3”. As the name implies, the strict nature of this type of NAT does not permit the ability to establish connections with other users.</translate> | ||
<!--T:12--> | <!--T:12--> | ||
For the best Resonite experience, it is recommended to configure your router in such a way to permit a | <translate><!--T:127--> For the best Resonite experience, it is recommended to configure your router in such a way to permit a moderate or Type-2 NAT from the computer running Resonite. Each manufacturer implements this configuration differently and the terminology is not often the same between brands. Please refer to the documentation for your particular router or ask for assistance in the #questions-help forum in the Resonite [https://discord.gg/resonite Discord] server.</translate> | ||
=== pfSense/OPNsense Configuration === | |||
If you are behind a [https://www.pfsense.org/ pfSense] or an [https://opnsense.org/ OPNsense] router, their default outbound NAT configurations will prevent Resonite from connecting to sessions using [[Networking Information#UDP Hole Punching (LNL NAT Punchthrough)|LNL NAT Punchthrough]]. While Resonite will fall back to using the [[Networking Information#LNL Relay Support for Strict NAT|LNL Relay]] in this case, it introduces overhead that can be avoided by configuring your router to allow these connections. | |||
[[File:PfSense NAT Configuration.png|alt=Screenshot showing how pfSense's Outbound NAT must be configured to allow Resonite's LNL NAT Punchthrough to work. |thumb|pfSense router configured to allow Resonite to perform LNL NAT Punchthrough successfully]] | |||
==== pfSense ==== | |||
# Log into your '''pfSense''' web interface. | |||
# In the navigation bar, click on '''Firewall''' and then '''NAT'''. | |||
# Click on the '''Outbound''' tab. | |||
# Under '''Outbound NAT Mode''', select ''Hybrid Outbound NAT rule generation.'' and click '''Save'''. | |||
# Next, click the first '''Add''' button underneath the '''Mappings''' section. | |||
# Next to '''Source''', change the ''Type'' dropdown from "Network" to "Any". | |||
# Scroll down and check the checkbox labelled '''Static Port'''. | |||
# Click '''Save''' at the bottom of the page. | |||
# Click the '''Apply Changes''' button at the top of the page. | |||
[[File:OPNsense NAT Configuration.png|alt=Screenshot showing how OPNsense's Outbound NAT must be configured to allow Resonite's LNL NAT Punchthrough to work.|thumb|OPNsense router configured to allow Resonite to perform LNL NAT Punchthrough successfully]] | |||
==== OPNsense ==== | |||
# Log into your '''OPNsense''' web interface. | |||
# In the left sidebar, click '''Firewall''', '''NAT''', and then '''Outbound'''. | |||
# Under '''Mode''', select ''Hybrid Outbound NAT rule generation'' and click '''Save'''. | |||
# The '''Manual rules''' section will appear. Click the '''+''' icon on the far right side. | |||
# Scroll down and check the checkbox labelled '''Static-port'''. | |||
# Click '''Save''' at the bottom of the page. | |||
# Click the '''Apply changes''' button at the top of the page. | |||
=== LNL Relay Support for Strict NAT === <!--T:13--> | === <translate><!--T:128--> LNL Relay Support for Strict NAT</translate> === <!--T:13--> | ||
Resonite provides a method for users who are using a router with | <translate><!--T:129--> Resonite provides a method for users who are using a router with strict NAT to connect to other users by using an intermediary server known as the Resonite LNL Relay. Although this solution will work for occasional use, it may not provide the best performance depending on geographic location and network load/congestion.</translate> | ||
<!--T:14--> | <!--T:14--> | ||
You can determine if you are connecting through an LNL Relay by the presence of the “LNL Relay” text appearing under the “Loading…” message while joining a world. The presence of the “LNL Relay” text when joining a world means that Resonite was unable to connect to the host user directly and the Resonite LNL Relay server was used. | <translate><!--T:130--> You can determine if you are connecting through an LNL Relay by the presence of the “LNL Relay” text appearing under the “Loading…” message while joining a world. The presence of the “LNL Relay” text when joining a world means that Resonite was unable to connect to the host user directly and the Resonite LNL Relay server was used.</translate> | ||
<!--T:15--> | <!--T:15--> | ||
The presence of the “LNL Relay” text typically indicates that either you, the host user, or both users may be behind a | <translate><!--T:131--> The presence of the “LNL Relay” text typically indicates that either you, the host user, or both users may be behind a strict / Type-3 NAT. If you see this message each time you connect to a world, there is a good chance that you are behind a router that is configured for strict / Type-3 NAT.</translate> | ||
<!--T:16--> | <!--T:16--> | ||
It is recommended to use a | <translate><!--T:132--> It is recommended to use a moderate or Type-2 NAT to avoid the dependency on using the LNL Relay. See the [[Networking Information#Recommended Router Configuration|Router Configuration]] section above for more information.</translate> | ||
=== uPNP/NAT-PMP and Port Forwarding === <!--T:17--> | === <translate><!--T:133--> uPNP/NAT-PMP and Port Forwarding</translate> === <!--T:17--> | ||
<!--T:18--> | <!--T:18--> | ||
Resonite does not currently offer support for port forwarding or uPNP/NAT-PMP. | <translate><!--T:134--> Resonite does not currently offer support for port forwarding or uPNP/NAT-PMP.</translate> | ||
Revision as of 21:55, 30 June 2024
Resonite is a feature rich engine that is connected both to other users and the Resonite cloud services. If you're concerned or have a firewall you'd like to configure then read on to find out more.
HTTP & WebSocket Traffic
Things like messages, profile information and items in your inventory are all stored within the Resonite cloud. Your copy of Resonite will use HTTP(S) or WebSockets to retrieve this information.
Here is a list of places you might see connections to:
- Most HTTPS Traffic is from
api.resonite.com - SignalR (real time updates) makes a WebSocket connection to the Microsoft managed service also at
api.resonite.com - Assets (avatars, meshes, textures etc.) and other blobs (large files) come from a variety of hosts:
- Asset variants are stored at
variants.resonite.comandskyfrost-archive.resonite.com/variants - Assets are stored at
assets.resonite.comandskyfrost-archive.resonite.com/assets - Thumbnails are stored at
thumbnails.resonite.comandskyfrost-archive.resonite.com/thumbnails
- Asset variants are stored at
Session Traffic
When you connect to a Resonite session, you're starting a connection to the session's host. This is usually another user's computer but sometimes can be a headless session which could be hosted in a number of places - two of the most common ones being on someone's spare computer or on a computer rented in a data center.
Depending on your settings and the settings of the session host you'll connect with either one of the following protocols:
- LNL (LiteNetLib)
- Steam Sockets. Sometimes called "Steam Networking Sockets", "Steam Network", "SNS" etc.
LNL
- LNL uses UDP to connect.
- Ports will vary and can be any port depending on the host as it lets the host pick a free port
- In other cases a relay will be used.
- After punch-through or relay, the actual connection to the user can be any IP or port.
Steam Sockets
Steam Sockets is a Valve created networking protocol. You can find information on it here
Establishing Connections
Resonite utilizes multiple methods to attempt to connect users to sessions on remote machines. This can be illustrated in the following flow chart.
Resonite will attempt to directly connect users where it can, for example over a LAN. However, this is not always possible due to a variety of network security constraints.
Direct IP
In general, direct IP is best. You’re connecting directly with the remote server and are telling Resonite exactly where to go and how to get there (you are connecting with a direct IP address or domain name).
To use direct IP
- Use an OpenWorld ProtoFlux node and add a Uri (purple input second from top) with the IP address and port like this:
lnl://<IPv4 address>:<Port>/- For IPv6, wrap the address in brackets
lnl://[<IPv6 address>]:<port>/ - You can also use a DNS record for this -
lnl://<domain>:<port>/
- For IPv6, wrap the address in brackets
- A port is currently required as part of the URL
- This is mostly applicable to headless sessions where the session has a static IP address and port. Keep an eye out for session owners providing items that include direct links for their worlds as that will be the most reliable and expedient way to connect to said world.
As an example for a session hosted with the IPv4 address 203.0.113.7, IPv6 address 2001:db8::7, the DNS record seven.example.com on port 12100:
lnl:///203.0.113.7:12100/: IPv4 direct connection
lnl://[2001:db8::7]:12100/: IPv6 direct connection
lnl://seven.example.com:12100/: DNS direct connection
UDP Hole Punching (LNL NAT Punchthrough)
UDP hole punching is used by LNL in Resonite in order to establish a bidirectional connection between you and a session host where Network Address Translation (NAT) is in play on one or both sides of a connection.
This is facilitated by one of Resonite's LNL punchthrough servers (the same hosts that can be seen in #LNL Relay), where both you and the host establish a connection in order to establish a peer to peer connection between you and the host that should be indistinguishable from directly connecting.
If you encounter issues with NAT punchthrough, you may be behind a Strict (also known as Type 3) NAT, where the conditions of the NAT make it so hole punching doesn't work.
You can check your NAT type by going to https://networktest.razortune.com/ in a web browser - this is a tool hosted by community member Rucio and is specific towards Resonite networking.
If your NAT type is Strict, there are two common causes for this:
- Your router could have settings in place for its NAT causing this to happen - what you want is a 1:1 NAT or a static NAT (terminology may differ depending on router)
- Your ISP could be doing CGNAT in a way that causes this - you can see if you're behind CGNAT by checking what your router reports your WAN address as being and what a site like https://ipinfo.io says; if these two addresses differ, you're likely behind CGNAT.
If it's your router:
Check your router settings - a good way to start is by searching "<router> Open NAT" and seeing what comes up setting wise.
If it's your ISP:
You may be able to contact your ISP to get them to either take you out from behind CGNAT or give you a static, public IPv4 address. This may come at a cost for something like a static IP.
If you're unable to resolve being in a strict NAT situation, it is recommended to use #Direct IP connections followed by using the #LNL Relay to connect to sessions.
Possible Bugs
- One current issue seems to be that the NAT punchthrough server occasionally does not respond very quickly, and the client does not always wait for a response and tries the next protocol on it’s internal list to attempt.
- The punchthrough server does not support IPv6, instead only supporting IPv4. Some ISPs in some parts of the world, such as Japan, use exclusively IPv6. Users in these networks may not be able to use NAT punchthrough (this gets very complicated very quickly, results will vary). (Github Issue #143)
LNL Relay
This can come with performance implications. The relay acts as a third point between both clients, and all traffic is routed through it. Ping will likely be worse here (but not always). If the relay has issues or is overloaded, you may also get service issues.
- We have the following LNL Relays
- uswest1.resonite.com - US West (Hillsboro, OR)
- au1.resonite.com - Oceania (Sydney, Australia)
- japan1.resonite.com - Asia Pacific (Tokyo, Japan)
- europe.resonite.com - Europe (Helsinki, Finland)
You can see the status of these relays at https://status.yellowdogman.com or in a raw format at https://api.resonite.com/networknodes
How LNL Relays Work
When a relay is required, the client sends a request to https://api.resonite.com/networknodes to retrieve the currently available relays. From there, the client makes a determination based upon multiple factors which relay is the best one for it to utilize. For example, the relay's currently available capacity, and its ping. The ports for the relay are determined by the relay server's operating system and port availability. Do not assume any consistency for the relays.
Here's a diagram illustrating the relay connection flow:
At this time, we do not support the ability to pick a specific relay.
Recommendations for Headless Servers
To better support direct connection conditions it is suggested server hosts try to promote direct IP connections and IPv6 support.
If you have a public IPv4 address that you can use, you can port forward the session's port. To do this, set the forcePort option for the world in your headless config file & forward the port through your router. You can find out how to do this by searching "<Router Model> port forward" - for most routers, you'll be able to find an example somewhere on the internet.
If you have IPv6 support, use it when possible by setting forcePort as in the IPv4 example, allowing the session's port through your firewall & direct connecting (See #Direct IP for how to directly connect to a session)
You may not be to port forward in all situations, such as if you're using a router that doesn't let you port forward or if you're behind CGNAT.
If you are behind CGNAT (Carrier Grade NAT), see if you can get off it - depending on your ISP and the type of your internet connection, you may get varying results. Some will take you off CGNAT if you ask, some will get you to pay for a static IP address and some may not allow you to get off CGNAT at all.
If you're having users with issues connecting via LNL punchthrough, direct them to directly connecting to your session. Making an object that connects them - such as a button that they can press and just connect makes doing this quite easy.
Recommended Router Configuration
Many consumer routers are configured by default to provide optimal connectivity for Resonite by routing traffic in such a way which permits the ability for users to directly establish a connection to other users on the Internet. However, some advanced routers employ a type of NAT (Network Address Translation) where port numbers are not preserved when communicating with other hosts on the internet. This type of NAT is often referred to as strict, or “Type-3”. As the name implies, the strict nature of this type of NAT does not permit the ability to establish connections with other users.
For the best Resonite experience, it is recommended to configure your router in such a way to permit a moderate or Type-2 NAT from the computer running Resonite. Each manufacturer implements this configuration differently and the terminology is not often the same between brands. Please refer to the documentation for your particular router or ask for assistance in the #questions-help forum in the Resonite Discord server.
pfSense/OPNsense Configuration
If you are behind a pfSense or an OPNsense router, their default outbound NAT configurations will prevent Resonite from connecting to sessions using LNL NAT Punchthrough. While Resonite will fall back to using the LNL Relay in this case, it introduces overhead that can be avoided by configuring your router to allow these connections.
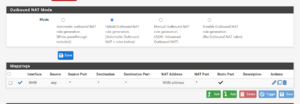
pfSense
- Log into your pfSense web interface.
- In the navigation bar, click on Firewall and then NAT.
- Click on the Outbound tab.
- Under Outbound NAT Mode, select Hybrid Outbound NAT rule generation. and click Save.
- Next, click the first Add button underneath the Mappings section.
- Next to Source, change the Type dropdown from "Network" to "Any".
- Scroll down and check the checkbox labelled Static Port.
- Click Save at the bottom of the page.
- Click the Apply Changes button at the top of the page.
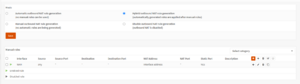
OPNsense
- Log into your OPNsense web interface.
- In the left sidebar, click Firewall, NAT, and then Outbound.
- Under Mode, select Hybrid Outbound NAT rule generation and click Save.
- The Manual rules section will appear. Click the + icon on the far right side.
- Scroll down and check the checkbox labelled Static-port.
- Click Save at the bottom of the page.
- Click the Apply changes button at the top of the page.
LNL Relay Support for Strict NAT
Resonite provides a method for users who are using a router with strict NAT to connect to other users by using an intermediary server known as the Resonite LNL Relay. Although this solution will work for occasional use, it may not provide the best performance depending on geographic location and network load/congestion.
You can determine if you are connecting through an LNL Relay by the presence of the “LNL Relay” text appearing under the “Loading…” message while joining a world. The presence of the “LNL Relay” text when joining a world means that Resonite was unable to connect to the host user directly and the Resonite LNL Relay server was used.
The presence of the “LNL Relay” text typically indicates that either you, the host user, or both users may be behind a strict / Type-3 NAT. If you see this message each time you connect to a world, there is a good chance that you are behind a router that is configured for strict / Type-3 NAT.
It is recommended to use a moderate or Type-2 NAT to avoid the dependency on using the LNL Relay. See the Router Configuration section above for more information.
uPNP/NAT-PMP and Port Forwarding
Resonite does not currently offer support for port forwarding or uPNP/NAT-PMP.